Discuss the Steps Involved in Modifying a Response File.
Many software products use settings in the response file to customize the installation of their particular product. Assignment Rubric 100 Points Sythesis of Concepts60Writing Standards APA Format20Timeliness20 This assignment is a summative assessment of the Course Objectives.

Renewal Of Saprouter Certificate Renew Microsoft Visual Studio Certificate
Windowsexe -options Cresponsefile -silent.

. Copy the appropriate response files from the clientresponse directory on the Oracle Database media to your hard drive. Cp directory_path responsedvrsp local_directory. The application and file analysis is performed to examine applications and files on a computer system to determine the perpetrators knowledge of and intent and capabilities to commit cybercrime for example the labelling or name of the file may indicate the contents of the file.
Step 2 Decision-Maker Exercise diligence in reviewing all materials provided as part of the Step 2 appeal Contact UHR and HRL for assistance. Location of the Middleware home. Runtime installation of Oracle Database Client.
To copy and modify a response file. In this example directory_path is the path to the database directory on the installation media. Copy the response file from the response directory to a directory on your system.
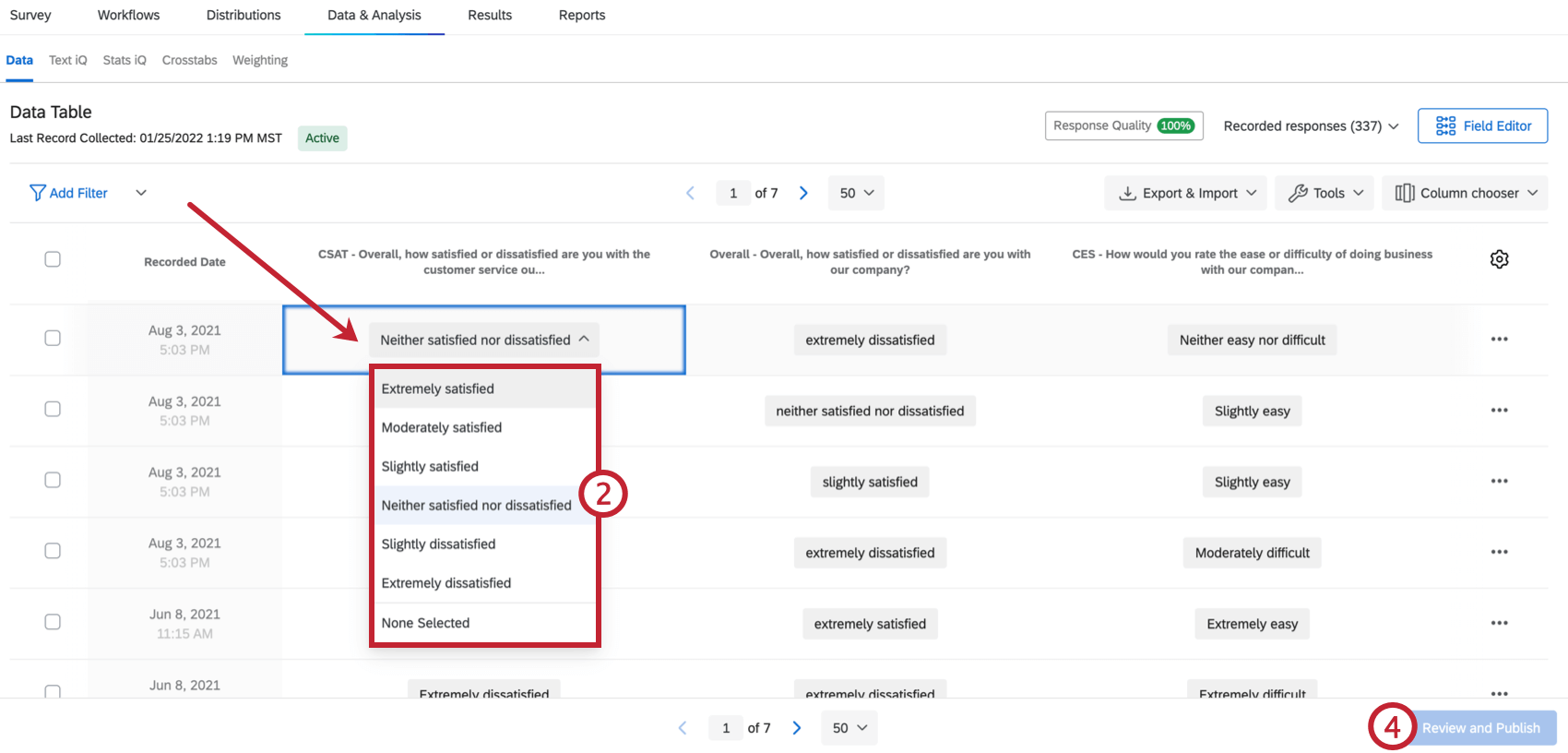
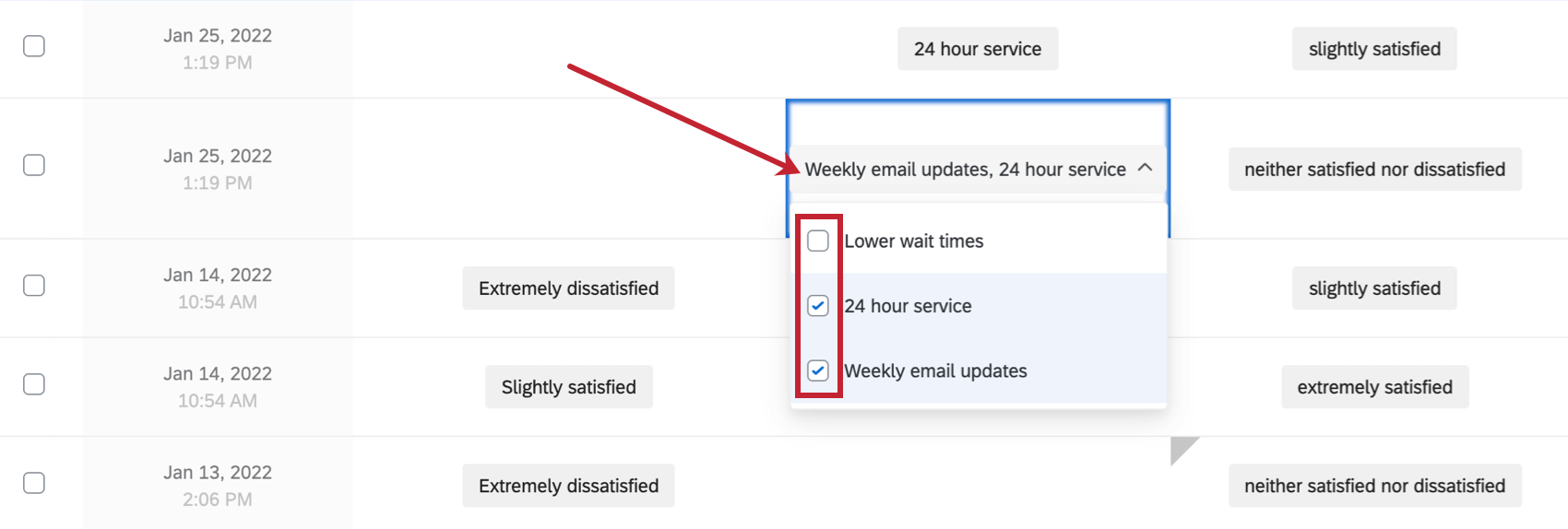
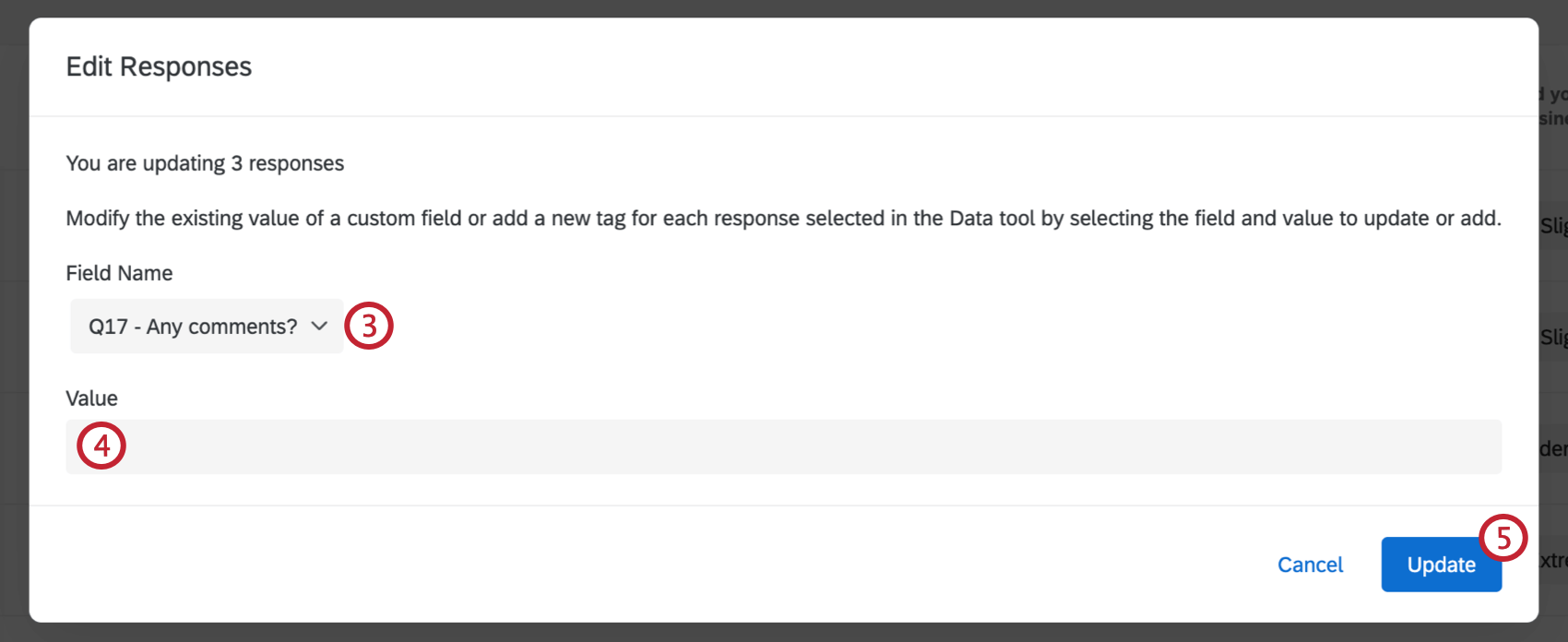
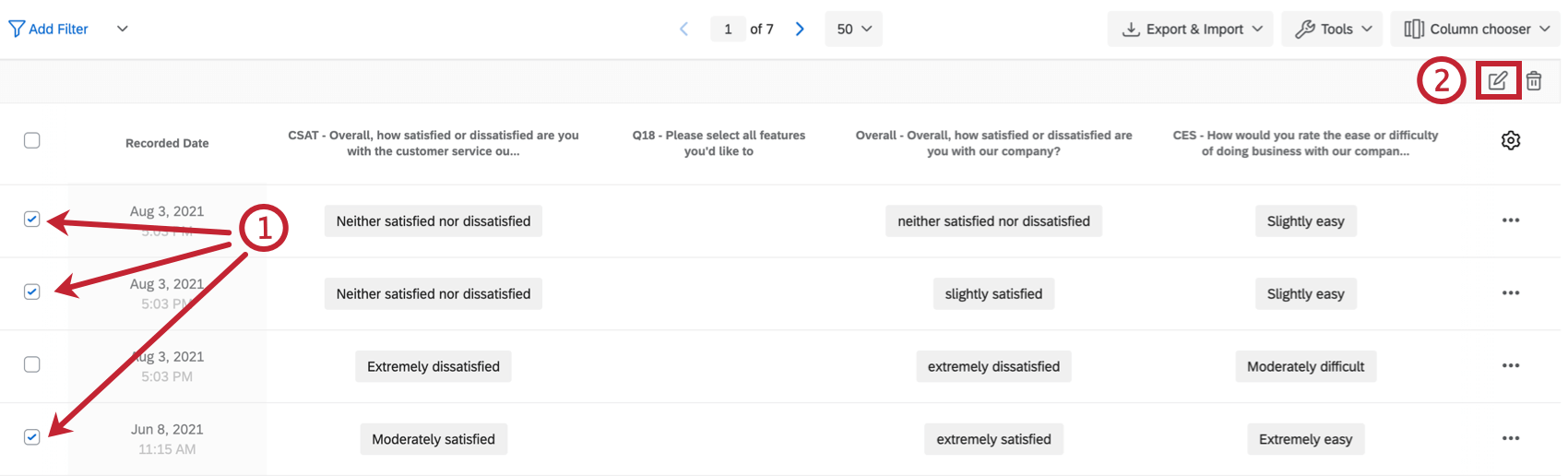
Modifying Response Files Edit the location of the repository as described in the preceeding text. After creating a customized response file the next step is to test it. Change the key attributes of the data elements that contain indications for.
On UNIX computers to generate the a. To modify the response file. Copy the response file from the response file directory to a directory on your system.
Copy the product installation files you downloaded to your computer. Copy the response file from the response file directory to a directory on your system. HARDWARE STUDY Determine Hardware and Software required to execute the application.
Please be sure to follow APA guidelines for citing and referencing source. There are five important steps that every response program should cover in order to effectively address the wide range of security incidents that a company could experience. These are the steps which would be taken to modify a response file.
Edit the file using the following options. Obtain the products response file template. Review any information provided in the response file or in the product installation guide.
Modify the response files with a text file editor. You can use this response file for silent mode installations. Go to the.
Review any information provided in the response file or in the product installation guide. Open the response file in any text editor. Cp directory_path response response_filersp local_directory.
Use the following steps to copy and modify the response file. In order for incident response to be successful teams should take a coordinated and organized approach to any incident. Determine Response time Volume of data to be processed Frequency of reports and then pick the hardware.
To copy and modify a response file. Nodename subdirectory under the SYSLOGIN directory which is where the oraInstloc file must reside. In this example directory_path is the path to the database directory on the installation media.
Use a responseats file. Create oralnstloc file by performing the following procedures. With the copy the admin needs to review the response file in depth to see what settings are already set Oracle 2002.
Previous What cautions woud you give students about multitasking. Discuss the steps involved in modifying a response file. Running the install silently with a response file is similar to the process of creating a response file - run the installation and provide a couple of command line parameters.
Once the file is found the admin should make a copy of the response file. Assure UHR has a copy of the appeal Within 10 calendar days of receipt of the appeal meet with EmployeeGrievant and discuss appeal Give EmployeeGrievant opportunity for oral. The dvrsp file is located in the response directory on the installation media.
The assignment must be a minimum of one 1 full page in length with a minimum of two 2 outside sources. Next Write a letter to families create a first-day information handout create a family information poster for your school or think of another way to share the information you would like families to know. The following steps are general steps involved in modifying a response file.
Incident response is a process not an isolated event. Discuss the steps involved in modifying a response file. For more information see Creating a Response File With Record Mode on page 3-3.
Make a copy of the products response file and open it in a text editor. Change the id attribute of the offering element to indicate the edition that you want to install. Discuss the steps involved in modifying a response file.
To copy and modify a response file. Make a copy of the products response file and open it in your favorite text editor. Insert the appropriate product installation disk and copy the contents of the disk to your computer.
To modify a response file. The file is in XML format. For example if you.
Cp directory_path response response_filersp local_directory. To use the response file that is provided with the installation go to the directory for your operating system and find the responseats file. Eg the file name can be the cybercrime victims name US.
STEPS INVOLVED IN SYSTEM ANALYSIS AND DESIGN LIFE CYCLE OF SYSTEMSANALYSIS AND DESIGN Steps involved in Analysis and Design 1. Discuss the steps involved in modifying a response file. To modify the response file.
In order to complete assignment 4 you will need to answer the below questions. Location of the Middleware home.
Take Response Actions On A File In Microsoft Defender For Endpoint Microsoft Docs

Steps To Install The Latest Squid Proxy Server On Ubuntu 20 04 Lts Proxy Server How To Uninstall Server

Time Word Problems What Time Should You Leave Time Word Problems Word Problems High School Special Education

10 Signs Your Wordpress Site May Be Hacked Cyber Security Website Security Web Security

How To Create The Perfect Checklist Inc Com Checklist Disaster Response Simple Sentence Structure
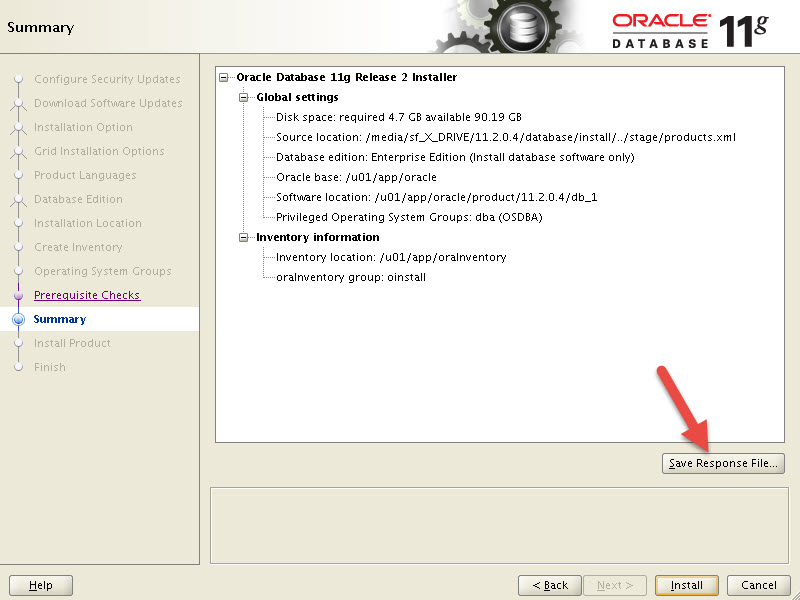
Oracle Base Oracle Universal Installer Oui Silent Installations

Take Response Actions On A File In Microsoft Defender For Endpoint Microsoft Docs
Response Requirements Validation
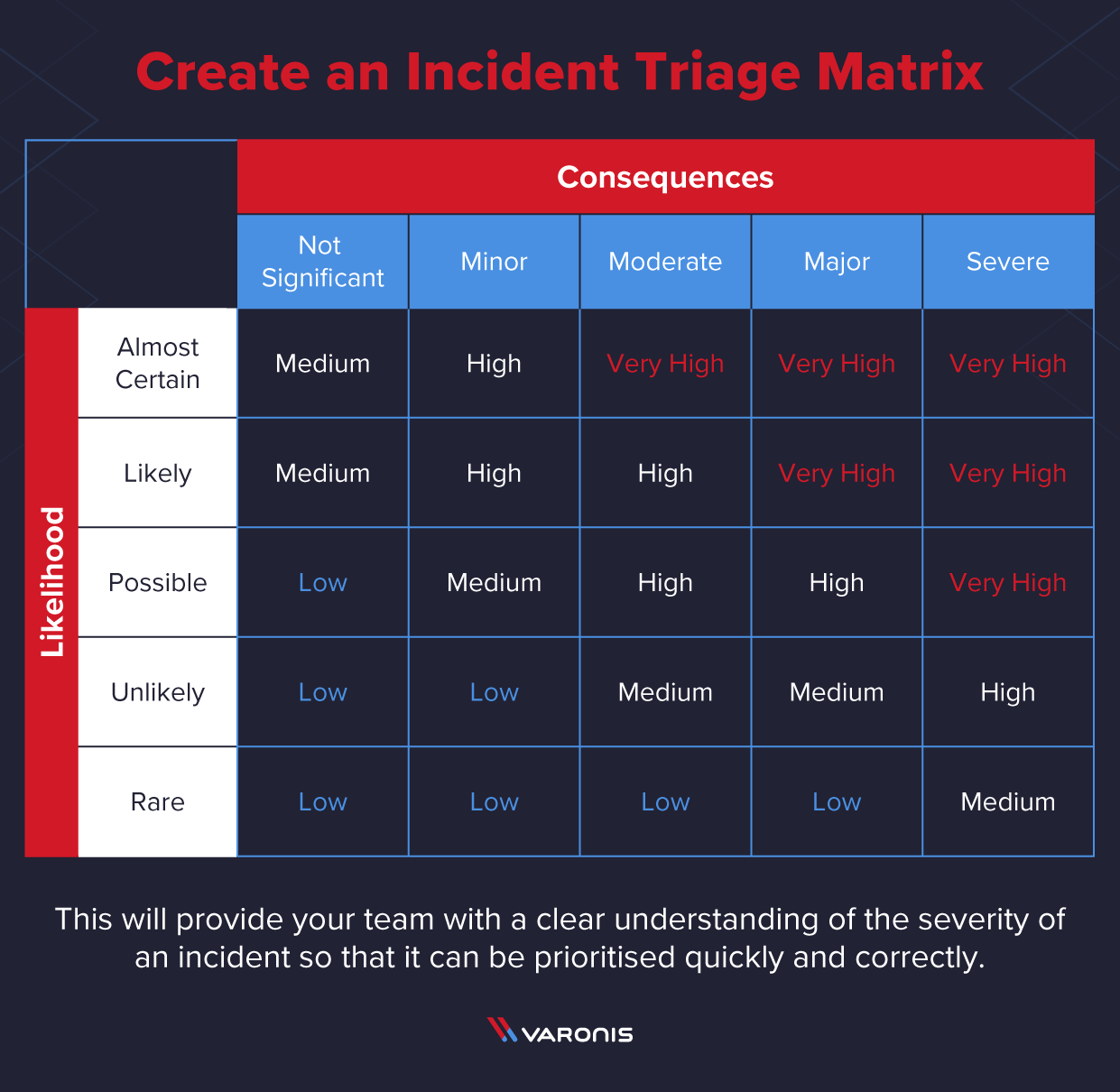
What Is An Incident Response Plan And How To Create One

Take Response Actions On A File In Microsoft Defender For Endpoint Microsoft Docs

How To Create The Perfect Checklist Inc Com Checklist Disaster Response Simple Sentence Structure

Draft Memo To Pm Prepared By Senior Pmo Staff Including Then Chief Nigel Wright Memo Preparation Lettering

Take Response Actions On A File In Microsoft Defender For Endpoint Microsoft Docs

Take Response Actions On A File In Microsoft Defender For Endpoint Microsoft Docs

Https Drawittoknowit Com Course Biochemistry Glossary Biochemical Pathway Glycolysis Review Glycolysis With This Fl Biochemistry Biochemical Science Lessons
Comments
Post a Comment